Caller ID spoofing is the act of maliciously faking the caller ID on a phone call. This is usually to increase the chances of the person being called answering the call and to take advantage of them in some way, perhaps to defraud them. For example, a bad actor may spoof the caller ID to be a number in the local area code of the person being called. This is distinct from changing the caller ID for legitimate reasons, for example if a call center is making a call on behalf of a business and is presenting the caller ID of the business.
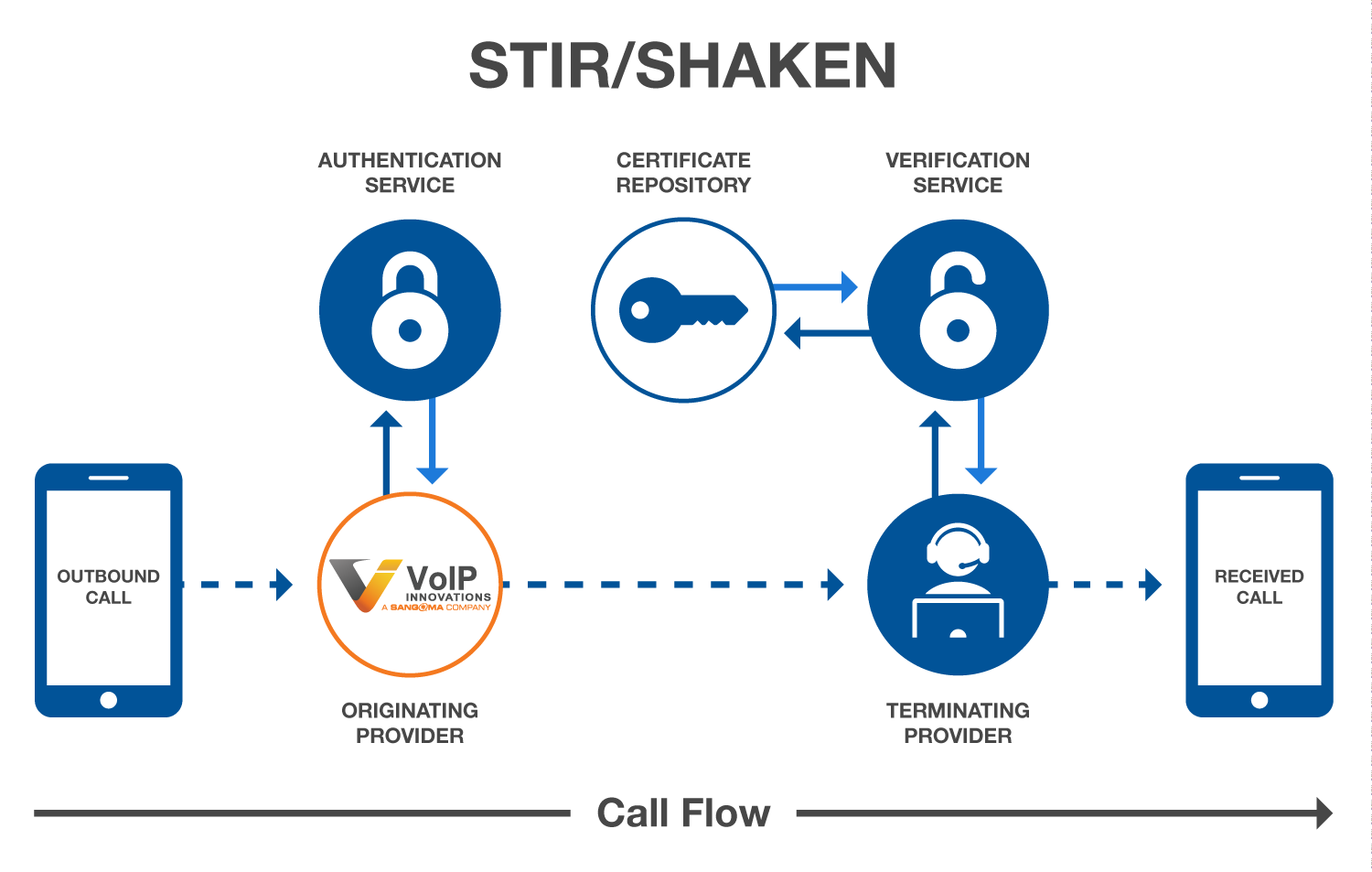
At a high level, STIR provides the ability within SIP to authenticate caller ID, and SHAKEN defines the end-to-end architecture to implement caller ID authentication using STIR in the telephone network. You can see a list of relevant standards and specifications here.
The first is to feed into the CVT (Call Validation Treatment), also known as Real-Time Analytics – see here for more background. As STIR / SHAKEN becomes more widely deployed in the telephone network, then Real-Time Analytics will be more empowered to tell the difference between spoofed calls and non-spoofed calls and will be better able to filter out the bad calls from the good, ultimately providing a better experience for subscribers.